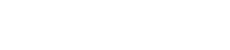You are going to receive spam email. No hardware or software solution, no spam filter is 100% accurate. You are constantly balancing spam rules between being too harsh and potentially dropping legitimate emails, or being too loose and drowning your users in junk mail.
With the rise of malicious attacks in recent years one of the best things you can do is educate users regarding the responsible use of email and how to recognise spam and malicious emails before they click on links, or even open the email. After all, it only takes one click to infiltrate a network, and in the case of the recent ANU data breach there was no action taken by a user and the network was still infiltrated via email.
Part of educating users about spam email is also giving them a helping hand. One mitigation and education tactic I have developed is to use mail flow rules to flag potential spam and warn users about the risky message in plain language, in the hopes they will treat the message with an increased level of scrutiny.
A particular issue that I faced was phishing attempts using email spoofing. Strategies that involved creating SPF rules and tightening spam rules greatly reduced the number of emails but they were still present. I suspect part of the issue was that these phishing emails were coming from other compromised Microsoft tenants and thus bypassing some of Microsoft’s spam filtering systems. To further complicate things, there was a need for some emails to be sent using the fqdn of the business from outside of the Microsoft tenant, so dropping all mail that originated outside of the Exchange server wasn’t an option.
The problem: Phishing emails that spoofed the users email domain were making is past spam filters and spf checks.
Here is what I did: Using Office 365 I have created the following mail flow rule in the Exchange admin center.
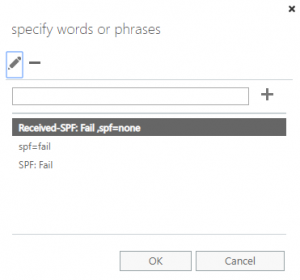 1. The rule was applied if the message header included the following words or phrases:
1. The rule was applied if the message header included the following words or phrases:
- Received-SPF: Fail, spf=none
- spf=fail
- SPF: Fail
2. I then restricted the rule to apply is the sender and recipient domain matched the domains used for email.
3. Prepend the message with the following disclaimer to the email to alert the user to the spam risk.
This email message is likely spam and is probably a phishing attempt to gain access to your account details. Do not click any of the links in this email without first checking with the IT department. <br><br> This email has not infected your computer and there is no risk that the sender has gained access to our systems. You can safely disregard and delete this message if it is indeed spam. <br><br> Regards,<br> IT Department
4. Prepend the subject to grab the users attention with this message: ALERT! LIKELY SPAM:
5. 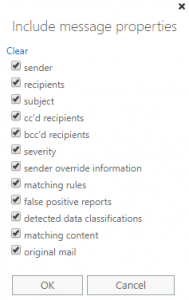 Lastly, generate an incident report and email it to myself so that I can keep an eye on the emails and follow up with the recipient if needed. Be sure to select to include ‘Custom content’ so you can review the original email and it’s contents.
Lastly, generate an incident report and email it to myself so that I can keep an eye on the emails and follow up with the recipient if needed. Be sure to select to include ‘Custom content’ so you can review the original email and it’s contents.
The screenshot below is what the rule looks like when completed.
6. The final thing to do is to educate users! Explain to them what a spam email looks like. Teach them how to check the senders address. Show them what this rule looks like when applied to an email. The users are your best asset and ally when fighting spam, and you should use them as such.
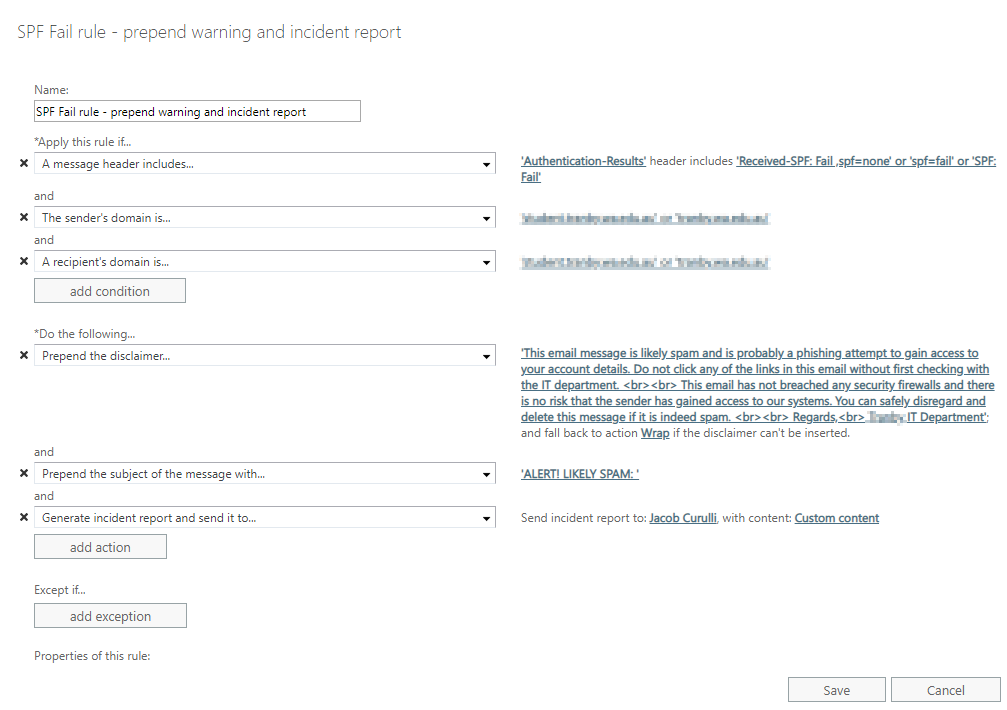
This is an example of the email message that a user would receive if this rule is triggered.
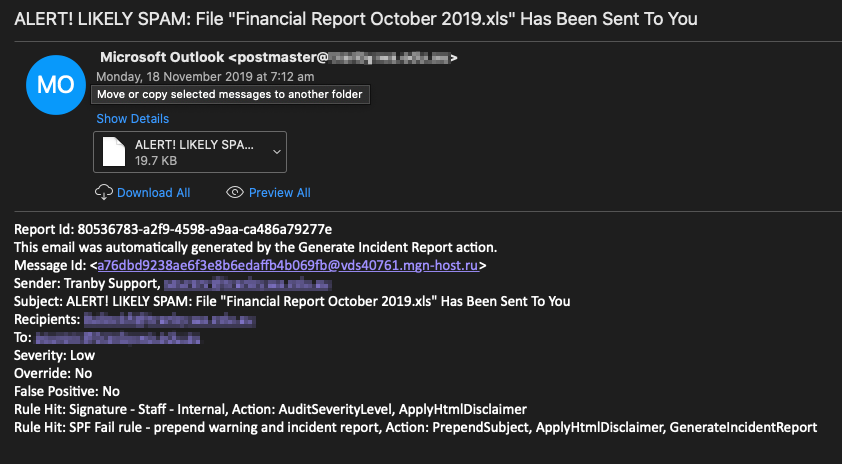
This is what the incident report looks like, with the suspect email sent as an attachment.